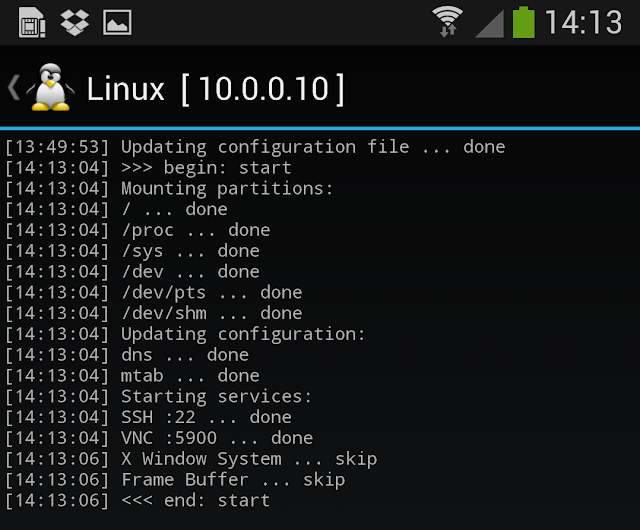
We all love our smartphones and tablets, but they go out of style so fast. With newer and more powerful gadgets coming out every six months or so, it doesn't take long for old phones to pile up around the house, especially if you’re on a family plan. You could recycle these old phones, or sell them, but we have a better idea. You should root it and turn it into a server for any one of the many needs you may have!
What is a server?
For those who don’t have much experience in IT or any complex computer technology, you may be thinking a server is exclusively those giant racks of hardware you see in data centers and high-budget techy action movies. In reality, a server is any computer designed to handle requests for information or files. Almost any computer can be converted to run as a server, and this includes Android devices. Even an old iPhone or iPad can be jailbroken and made into a server, but we’ll save that for another guide.
What kinds of servers can I run?
There are several types of servers you can run on Android that each have different abilities, and many free and paid apps that will get you there. To run as a server, your Android device needs to know the ‘protocols’ to share information. Each protocol is a set of connection rules that all computers or applications follow in order to connect to your server.
There are three main types of servers you can run on Android.
Web server
A Web server what you’re visiting right now. Every website runs off of a Web server. Android can act as a Web server because it requires very little processing power to run a site. You can use it to host a family site or just storing pages locally. A Web server uses the HTTP protocol and while is easy for Android to run, may be difficult to setup depending on what you want to do with it.
File Server
A file server is pretty straightforward and easy to run because all it does it create a directory where you can upload and download files from. While Android devices don’t have too much space, many can be expanded with MicroSD cards or external storage and a file server is a great way to store files of all shapes and sizes with it. A file server typically uses the FTP protocol.
Media Server
A media server is probably the coolest and most interesting thing you can make your Android device into, but is also the most complex. A media server allows your Xbox, PS3, PC, or other devices at home to connect and watch videos, listen to music, and more from your Android phone or tablet, where these files are stored. It’s a sort of advanced version of a file server and uses a number of different protocols, such as DLNA, to allow your other home gadgets to connect to it and stream files.
Other types of servers
There are other types of servers you can run specific to what your needs may be. A quick
Google search or look on the Play Store will tell you if the kind of server you want to run is possible. Some of the apps we highlight can also run these other types of servers you may be interested in. There are also some server types (such as a mail server) that are too difficult to easily explain or instruct on how to properly setup without encountering some challenging networking tasks.
What apps should I use?
In order to suit your needs, we’ve highlighted a few apps below that can help you get things started. All of these applications can run or several of the above types of servers and are either free or fairly priced. They all run about the same with a similar way to setup your servers of choice, but we’ll guide you along for each one:
Servers Ultimate
Servers Ultimate (pictured left) is the most feature-rich and effective server application for Android. It offers an intuitive interface that makes it easy to start and stop servers. From the home screen you can add servers, remove servers, and configure more than 60 server types it offers to your preference. This makes Server Ultimate a great option for all types of servers, though it does cost $9 after a limited 14-day trial.
Depending on what you want to do, Servers Ultimate has a number of server types to suit your needs ranging from HTTP for Web servers, FTP for file servers, and DLNA for media servers. Each server type has specific configurations you will need to walk yourself through in order to figure out which one is to your preferred configuration. Unfortunately it’s hard to guide you along each of the 60+ servers that Servers Ultimate has, but they all run the same way – you click the first icon on the home page to choose a server and then you choose which server you want to run. If you need a Web server, run the Web server function; if you want an FTP server, then run the FTP server. Servers Ultimate offers a really robust set of features for them all.
FTPServer
Per its name,
FTPServer is a pretty simple and easy-to-use FTP server for your Android device. In order to set up a file server you need to configure it with your username and password of choice, set a default directory, and then connect with an FTP Client to begin adding and removing files of your choice. This application is free and good for adding and removing files for download from your Android device. It can also be set to run at start up to ensure constant accessibility. FTPServer also allows more specific controls for restricting access or permitting access from certain Wi-Fi networks to ensure safe usage. Once you have all your settings tweaked to your heart’s content, click “Save and Restart Server” at the bottom to get started.
Pixel Media Server
Pixel Media Server is a really simple DLNA Media Server, meaning it lets your Xbox and other media devices stream content from your Android. In order to run it, you simply need to run the application and change two settings: the display name of your device and the folder that holds all of your media files (music, movies, pictures, and so on). Once you do that, start the server with the ‘Play’ button on the bottom, and you should be all set! This app is also free and a quick way to get a DLNA server running for streaming media files around the house. One warning: you will need to turn off sleep mode for your Android device with Pixel Media Server or you may encounter problems while trying to stream content.
These three apps are just a taste of the dozens of apps on Android that can be used to run dozens of types of servers including those mentioned in this guide. The best thing you can do is experiment to figure out just which app does what you want and meets your needs.
Final tips
Here are few (more complicated) tips to ensure your server works right:
- Your Android server will have a local IP address assigned to it, but your entire network will have its own an external IP address assigned to it. If you are using your server locally then connect with your device’s local IP address. You need to ensure you enter the right port for each server or it won’t properly connect.
- You may need to setup port forwarding on your home’s router in order to make the servers work effectively. Port forwarding ensures your router allows other devices on your network to see the port you’re running your server through. You can learn more about port forwarding from here.
- In order to use any of these servers outside of your home network you will need to use something called Dynamic DNS and buy a domain name. Dynamic DNS is very finicky and you can encounter a number of networking problems depending on your Internet Service Provider and the type of router you use. It allows your external IP address to be routed to a domain name you can easily remember. If you use Dynamic DNS, you can really only use one server for every set of ports. Having two devices both running servers on port 80 for example will cause serious problems.
- Rooting your device may not be necessary for all of these features, but we highly recommend doing it as a precaution.
That about covers it. If you have specific questions feel free to leave a comment and we’ll do our best to help or direct you to a better source for advice. This process can be simple or complex, depending on the kind of server you plan on creating, so keep in mind that you may want to try a simple file server before doing something more advanced, like a Web server or media server. Nonetheless, take advantage of all your Android device has to offers, and best of luck!
Source : digitaltrends