How a malware can steal the data from an infected system that doesn't have internet connection? You might think it is impossible. Computer scientists say it is possible.
When security researcher Dragos Ruiu claimed malware dubbed “badBIOS” allowed infected machines to communicate using sound waves alone—no network connection needed—people said he was crazy. New research from Germany’s Fraunhofer Institute for Communication, Information Processing, and Ergonomics suggests he’s all too sane.
As outlined in the Journal of Communications (PDF) and first spotted by ArsTechnica, the proof-of-concept malware prototype from Michael Hanspach and Michael Goetz can transmit information between computers using high-frequency sound waves inaudible to the human ear. The duo successfully sent passwords and more between non-networked Lenovo T400 laptops via the notebooks’ built-in microphones and speakers. Freaky-deaky!
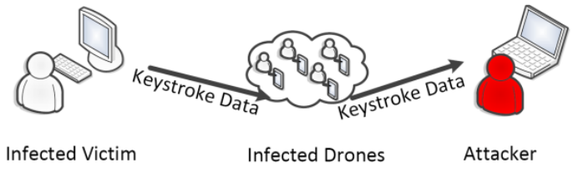
" The infected victim sends all recorded keystrokes to the covert acoustical mesh network. Infected drones forward the keystroke information inside the covert network till the attacker is reached. "
Sending data via sound
When security researcher Dragos Ruiu claimed malware dubbed “badBIOS” allowed infected machines to communicate using sound waves alone—no network connection needed—people said he was crazy. New research from Germany’s Fraunhofer Institute for Communication, Information Processing, and Ergonomics suggests he’s all too sane.
As outlined in the Journal of Communications (PDF) and first spotted by ArsTechnica, the proof-of-concept malware prototype from Michael Hanspach and Michael Goetz can transmit information between computers using high-frequency sound waves inaudible to the human ear. The duo successfully sent passwords and more between non-networked Lenovo T400 laptops via the notebooks’ built-in microphones and speakers. Freaky-deaky!
" The infected victim sends all recorded keystrokes to the covert acoustical mesh network. Infected drones forward the keystroke information inside the covert network till the attacker is reached. "
The most successful method was based on software developed for underwater communications. The laptops could communicate a full 65 feet apart from each other, and the researchers say the range could be extended by chaining devices together in an audio “mesh” network, similar to the way Wi-Fi repeaters work.
While the research doesn’t prove Ruiu’s badBIOS claims, it does show that the so-called “air gap” defense—that is, leaving computers with critical information disconnected from any networks—could still be vulnerable to dedicated attackers, if attackers are first able to infect the PC with audio mesh-enabled malware.
Sending data via sound
“We use the keylogging software logkeys for our experiment,” they wrote. “The infected victim sends all recorded keystrokes to the covert acoustical mesh network. Infected drones forward the keystroke information inside the covert network till the attacker is reached, who is now able to read the current keyboard input of the infected victim from a distant place.”
In another test, the researchers used sound waves to send keystroke information to a network-connected computer, which then sent the information to the “attacker” via email.
Now for the good news: This advanced proof-of-concept prototype isn’t likely to work its way into everyday malware anytime soon, especially since badware that communicates via normal Net means should be all that’s needed to infect the PCs of most users. Nevertheless, it’s ominous to see the last-line “air gap” defense fall prey to attack—especially in an age of state-sponsored malware run rampant.
Source : pcworld.com















0 comments:
Post a Comment